1. What is it Link to heading
Palo Alto has the capabilities to match traffic based on Application (Layer7).
However most internet traffic is now encrypted with SSL, this means that Palo Alto dont see the underlying application on encrypted traffic.
Decrypting trafic has an impact on how we configure AppID.
Also, We will see in this post the impact decryption has on security profile: URL filtering, Antivirus and other profiles.
2. Why do this Link to heading
One of the main goal of doing decryption is to get visibilty on encrypted trafffic.
This visibility help us to control, understand and apply ngfw features on it.
Using decryption will helps us to see the underlying application on encrypted traffic and to enforce more granular security policies.
Decryption with also helps us to analyze and block threat that are hidden behind encrypted traffic.
3. Diagram Link to heading
This is the same Lab as created in the other video previously.
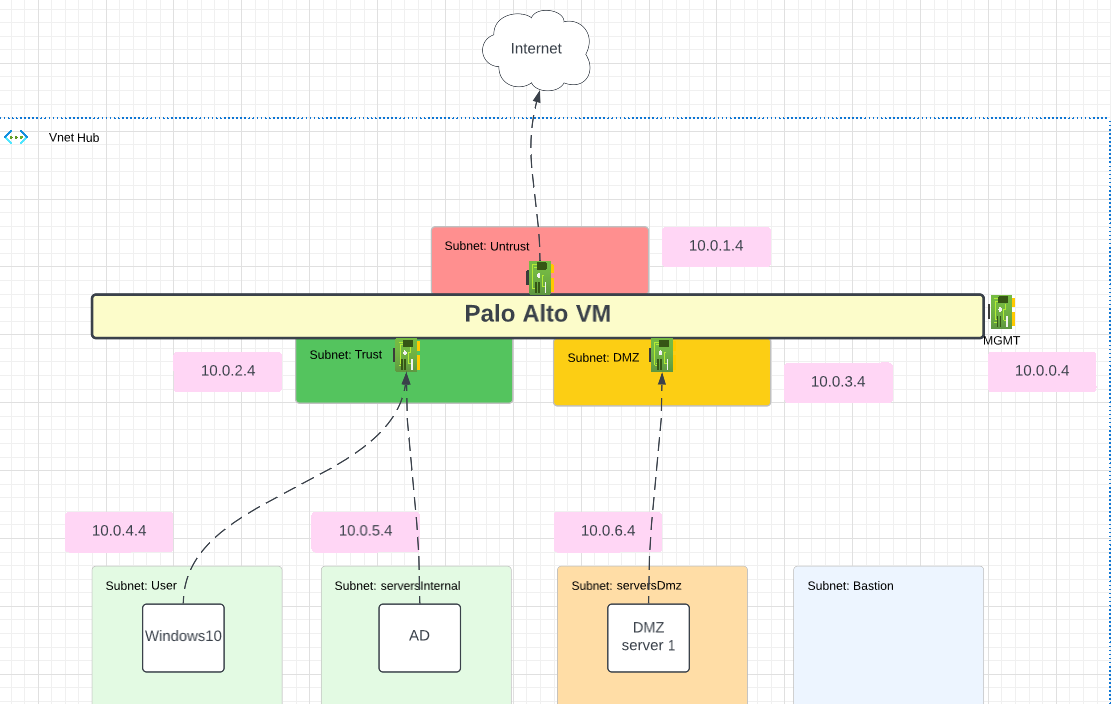
The default route for W10 and AD is the Trust NIC of the Palo Alto in Azure.
To follow me with this lab, you can go to my other post that show how to deploy that lab in Azure with Terraform: Lab Deployment Post
To configure decryption uses one of the following:
4. Lab Link to heading
4.1 AppID impact Link to heading
In this lab I will show you a simple usecase of the kind of granularity you can get with AppID using decryption.
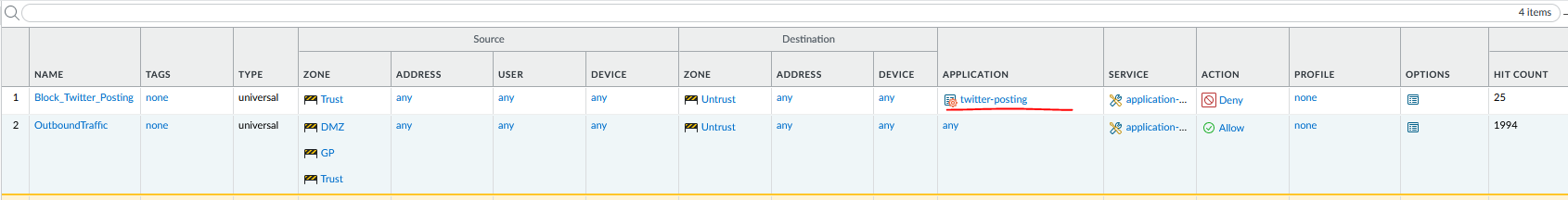
First we will start without using decryption and we will try to block the applicaiton: Twitter-Posting.
I create a security policy to block that specific AppID and put it above my general outbound security policy.
Also, I will disable my decryption policy, making sure there is no decryption happening.
Now Ill get on Twitter and try to post something.
Its working
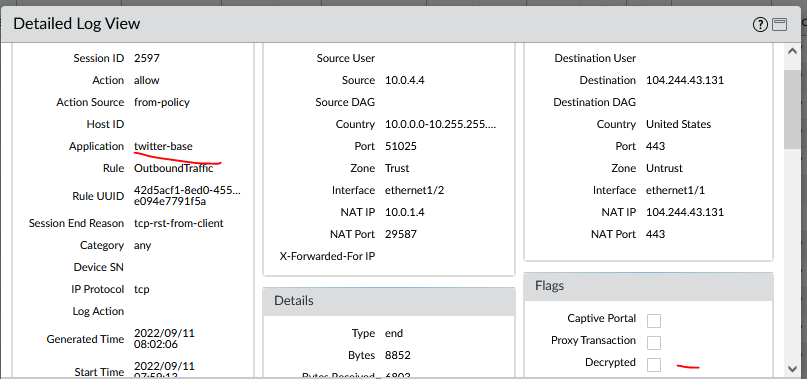
lets check the Palo Alto traffic logs
We can see that Palo recognize the app as being twitter-base, but unable to dig deeper to see whats the underlying application.
Now, lets enable decryption and test again.
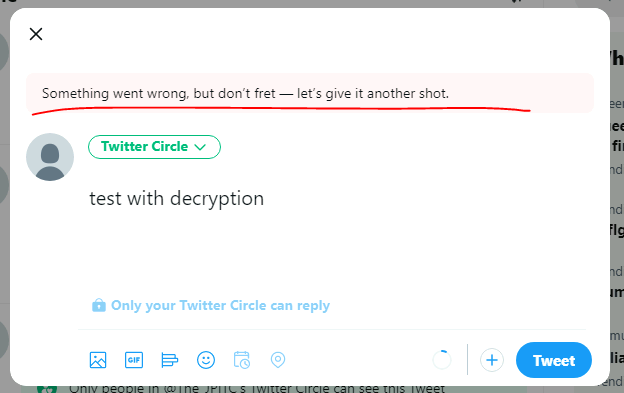
We are unable to post, lets check the Palo.
We see that Palo is now able to recognize the application: Twitter-Posting, and blocking the session.
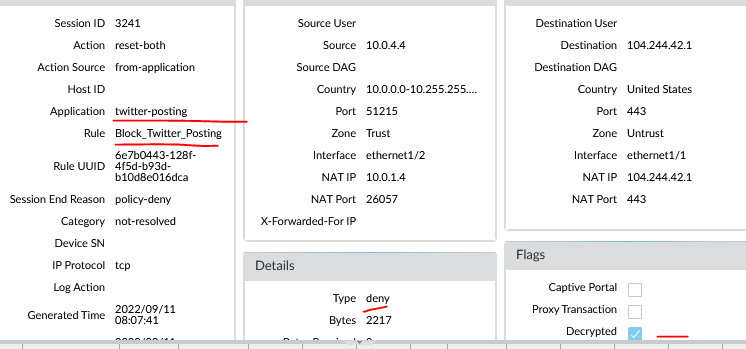
We can conclude that using decryption allow us to create more granluar security policies based on application filtering.
4.2 Security profile impact Link to heading
4.2.1 URL filtering Link to heading
Palo Alto behaviour when dealing with URL is different with and without decryption.
With encrypted traffic: Palo will use the SNI in the certificate to decide to allow/block.
With decrypted traffic: Palo will use the HTTP host and URL path.
Lets test this by creating a custom URL category with a URL Path in it.
jeremypageitcompany.com/posts/palo/posts/decryption_profile/
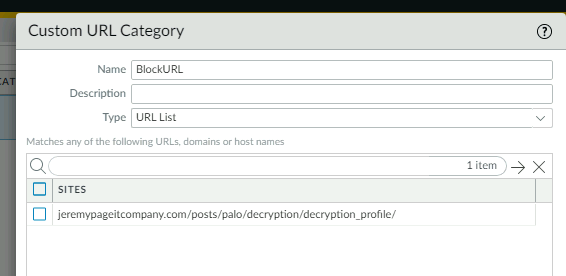
We can then use URL as a destination matching criteria or as a security profile.
Ill test it as a destination matching criteria of a security policy with an action of Deny.
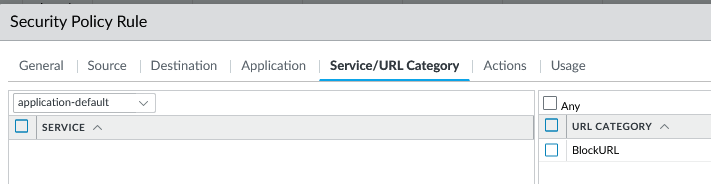
If I open a browser and go to this exact URL, with decryption enable, Palo block the site.
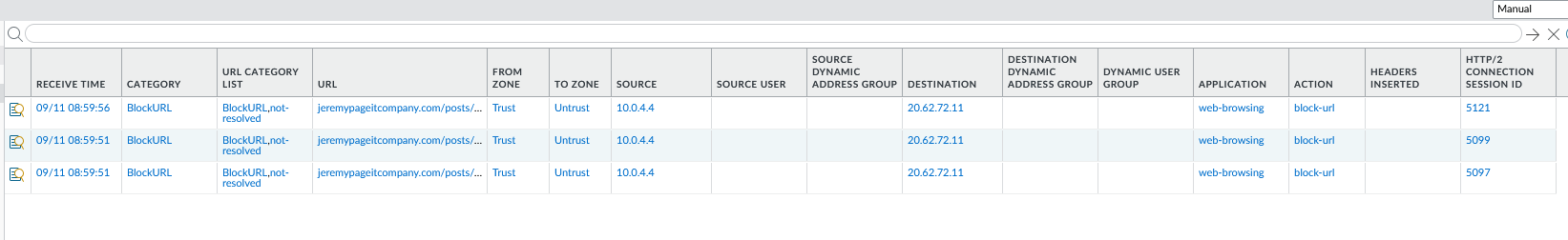
 We can check the URL filtering logs
We can check the URL filtering logs
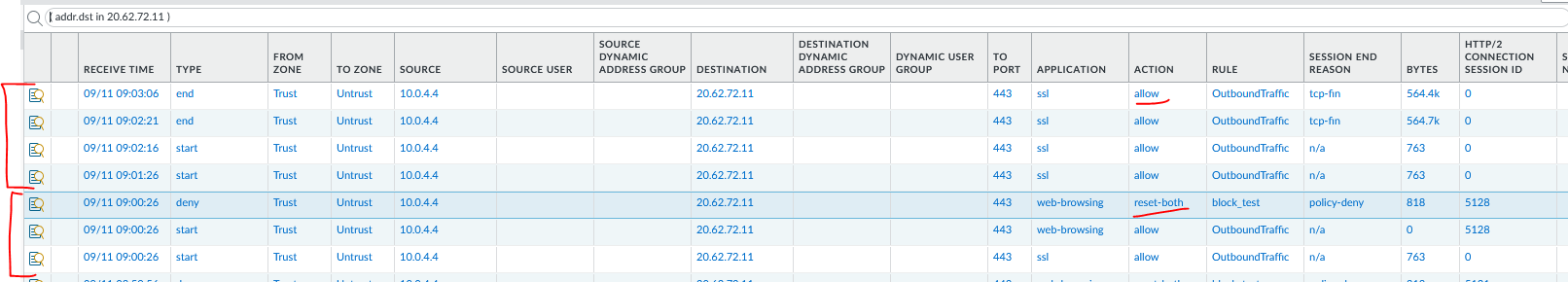
Now if I disable decryption and test again, I can go to the webpage, Palo is unable to block the recognize the full path and apply the correct sec policy.
4.2.2 Antivirus Link to heading
Now we will test the default Antivirus profile.
This profile will be apply to the outbound security policy.
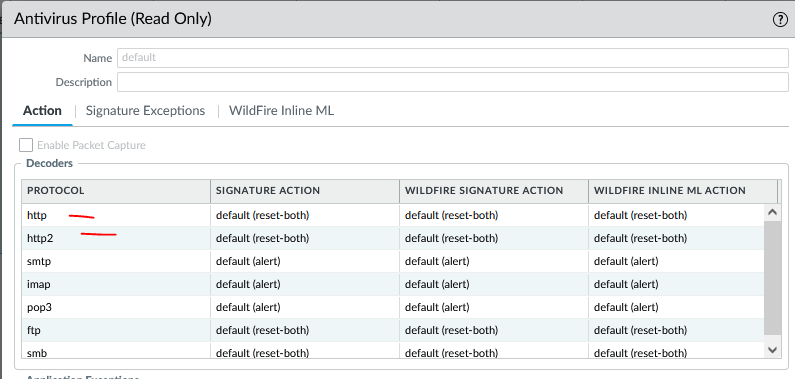
First lets try to download an Anti-Malware test file on eicar
Without Decryption, Palo Alto is unable to apply the Antivirus profile on encrypted traffic.
Lets enable decryption and try again.
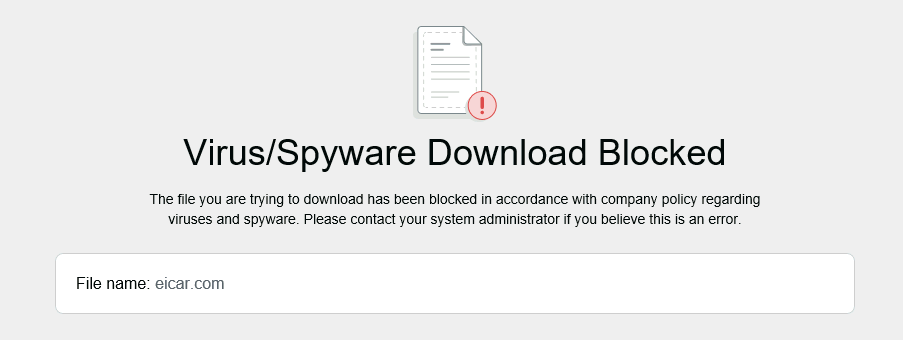 Palo Alto is blocking the session and inserting a response page to the user.
Palo Alto is blocking the session and inserting a response page to the user.
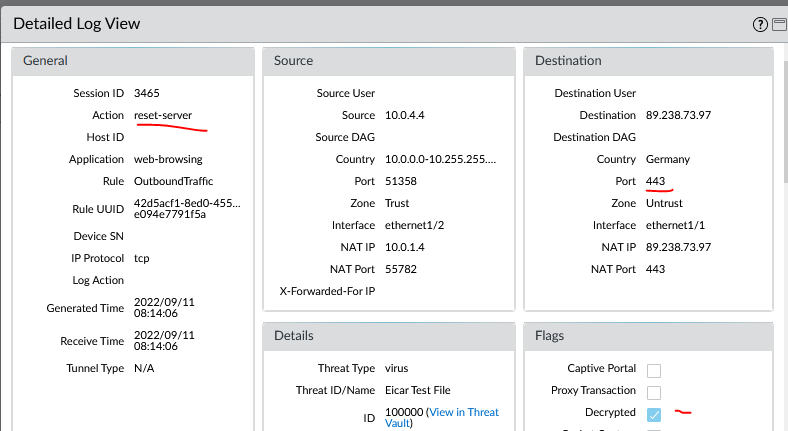
We can see in the Threat logs that the session was decrypted and blocked.
4.2.3 Other profiles Link to heading
Vulnerability protection Link to heading
This profile can be really usefull to block attack against known exploit.
A good way to leverage this is to use this profile on Inbound (DNAT) connections coming from the internet on exposed server.
However, to be effective on TCP443 for a web server, it require Inbound Decryption to be able to analyze the traffic.
Wildfire Link to heading
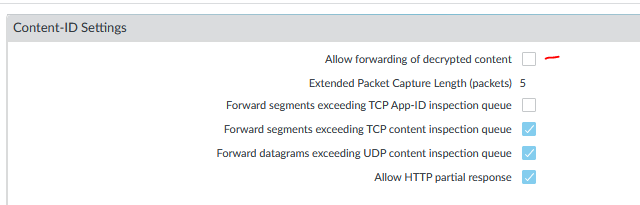
Wildfire is a great tool to analyze file and stop malware.
There is an option to forward decrypted traffic to Wildfire engine for inspection.
DNS Security Link to heading
This is one of the profile that does not need decryption to works as DNS traffic is not encrypted by default.
Misc Link to heading
Basically all other profile dealing with SSL will require decryption to be effective.