1. What is it Link to heading
Instead of using an Enterprise PKI to sign a subordinate CA for domain registed marchine, using a self-sign CA for decrytpion.
We will generate a Root CA on the Palo and a Sub-CA as well that will be configured as Forward Trust proxy, the Root CA will need to be push to the machine that we want to do decryption.
We will test different way to push the certificate to the machine
- Manually
- Global Protect
2. Why do this Link to heading
- for machine/user not registered to the AD domain
- Guest
- BYOD
- for POC and lab
3. Diagram Link to heading
This is the same Lab as created in the other video previously.
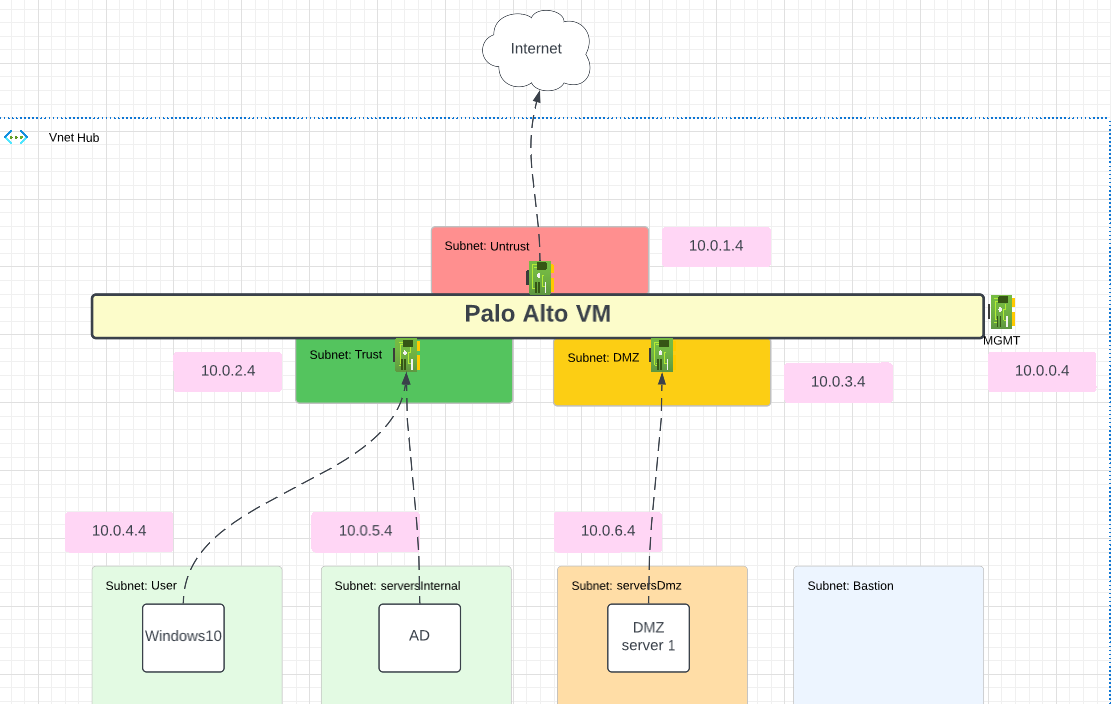
The default route for W10 and AD is the Trust NIC of the Palo Alto in Azure.
To follow me with this lab, you can go to my other post that show how to deploy that lab in Azure with Terraform: Lab Deployment Post
4. Lab Link to heading
4.1 Palo Alto Link to heading
4.1.1 Create certificate Link to heading
Let’s start by generating a Root CA on the Palo Alto.
This is the certificate that will be push to the user machine.
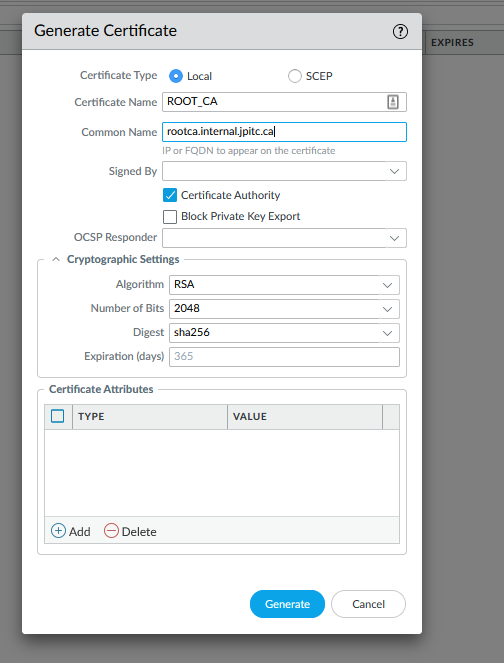
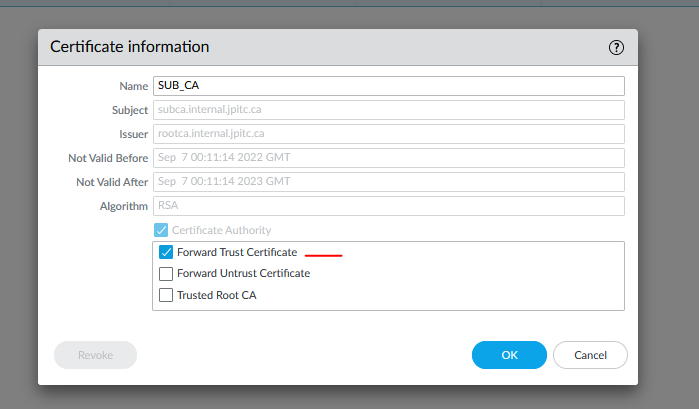
Now generate a new CA and use the Root CA to sign it, this one will be use to do Forward Trust Proxy.

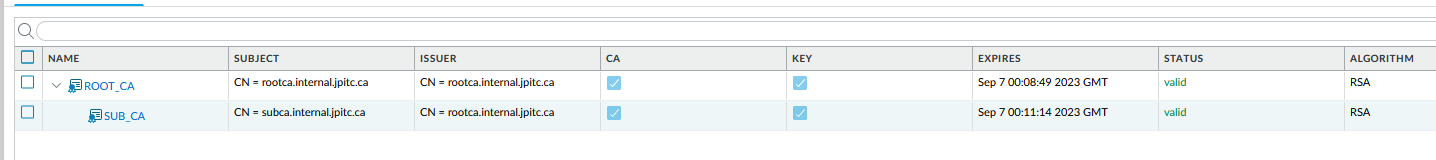
Configure the sub-ca to be a Forward Trust Certificate (Palo Alto will use this one for decryption to sign new certificate)
Also, we will configure an Untrust CA that will be used to sign certificate that are not trusted by the palo alto (expired, self-signed etc)
This one will not be sign by the RootCA
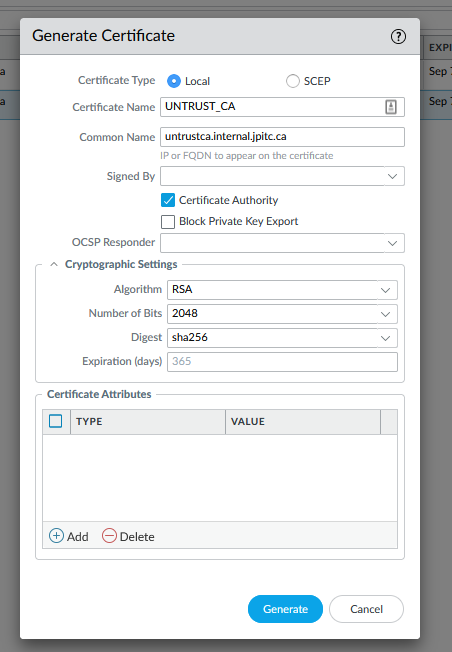
and will be configure as a: Forward Untrust Certificate

4.1.2 Create a decryption policy Link to heading
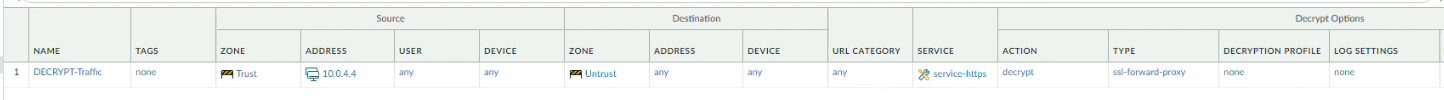
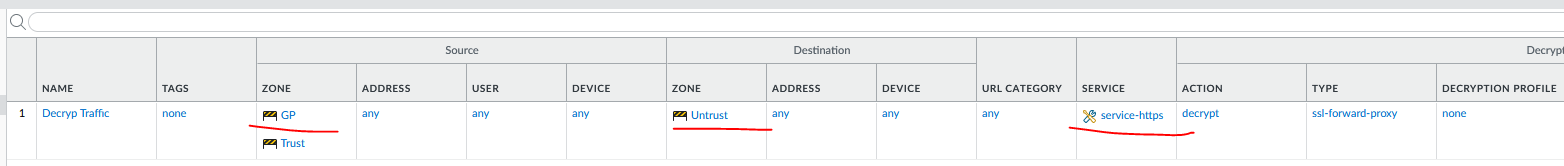
We will create a simple decryption policy to decrypt the traffic.
For this lab, the source IP will simply be the IP of the Windows10 machine.
Name: Decrypt Traffic
Source Zone: Trust
Source IP: 10.0.4.4(W10 machine)
Destination Zone: Untrust
Service: service-https(TCP443)
Action: Decrypt
Type: SSL Forward Proxy
Decryption Profile: None
Log: Successful/Unsuccesful SSL Handshake
Commit the changes
4.2 Push certificate Link to heading
Now lets make a test with the W10 machine.
Open a browser and go to any website, you should have a warning.
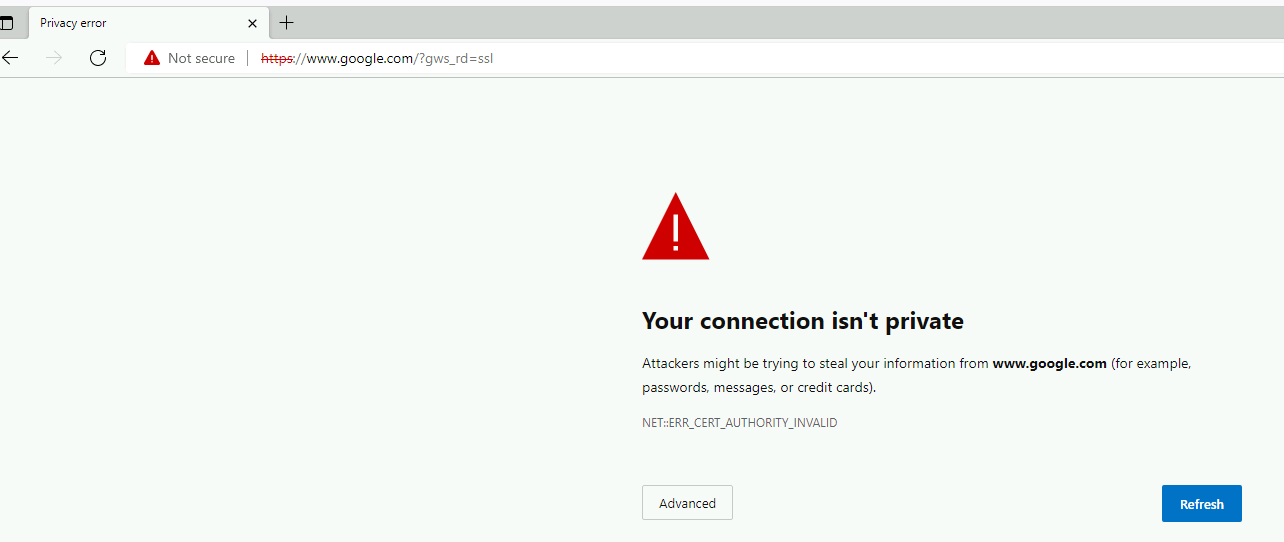
The reason is that Palo is using the sub-ca to sign the certificate presented to the browser.
but the browser does not trust either the sub-ca or the root-ca since its not in its store.
4.2.1 Manual import Link to heading
now lets download and install the Root-CA manually on the W10 machine.
Connect to the palo from the W10 machine.
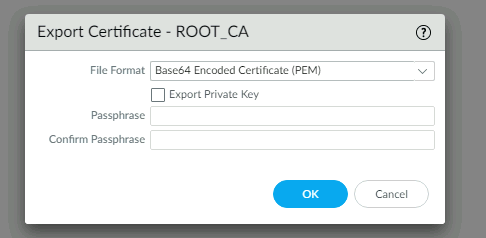
open the file and click on: Install Certificate…
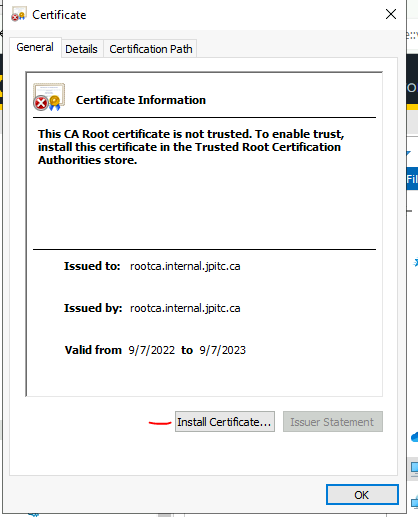
Current User: only apply to this windows user
Local Machine: apply to all user of the machine
choose to install the certificate in: Trusted Root Certification Authorities
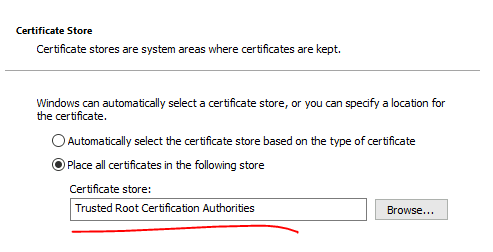 Click yes on the certificate warning
Click yes on the certificate warning
Validate that the cert is in the store, run
- certlm.msc (local machine)
- certmgr.msc (user)
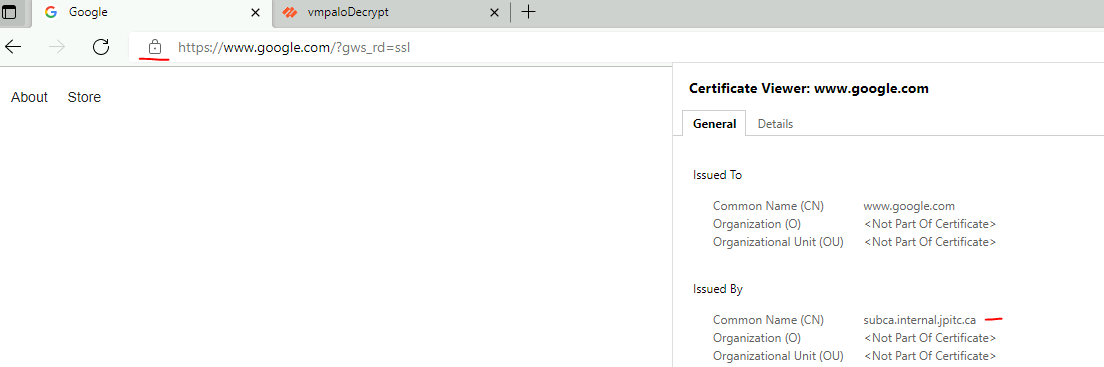
Validate a new website
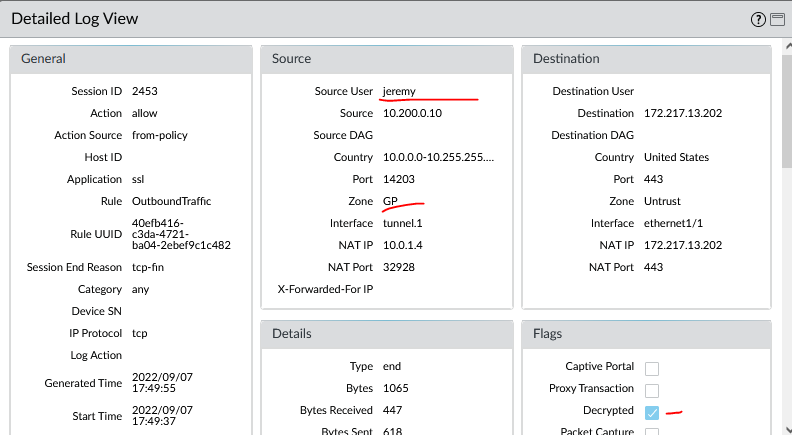
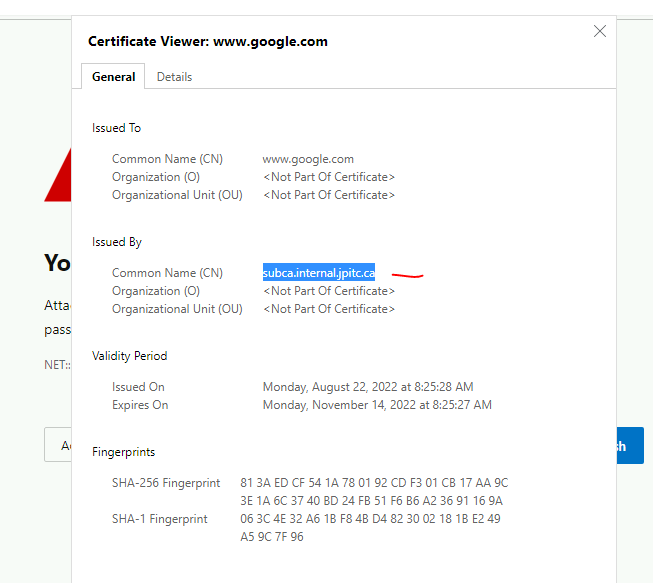
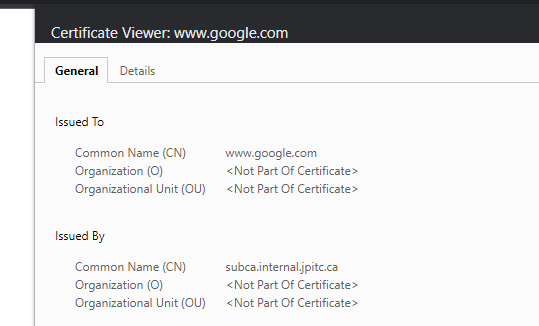
It should be working, check the issuer: subca.internal.jpitc.ca
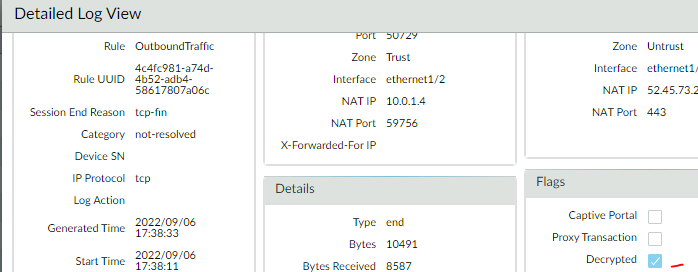
Check the detailed log session information, decrypted: check
4.2.2 Global Protect Link to heading
Manually importing the certificate on each of the machine can be a long process.
Another way to do this is to push the certificate (ROOT_CA) to the machine connecting to GlobalProtect.
With a working GP configuration, where GP users internet traffic is going through Global Protect:
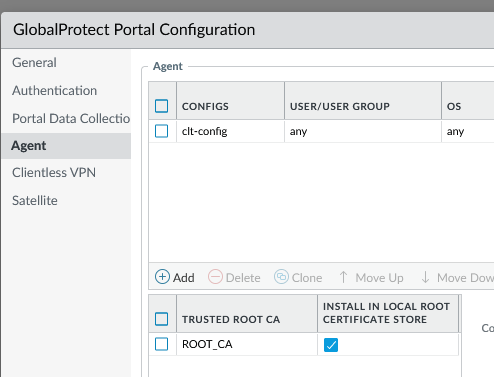
Go into your GP portal, click on Agent and add the Root CA used to sign the Sub-CA as a Trusted Root CA
- check: Install in Local Root Certificates Store.
You will also need to adapt the decryption policy to decrypt GP traffic
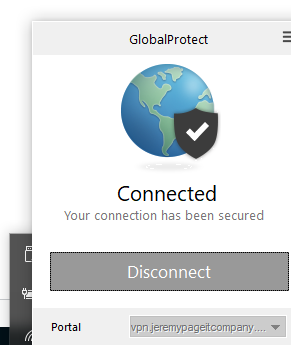
Connect to Global Protect and check your certificate store.
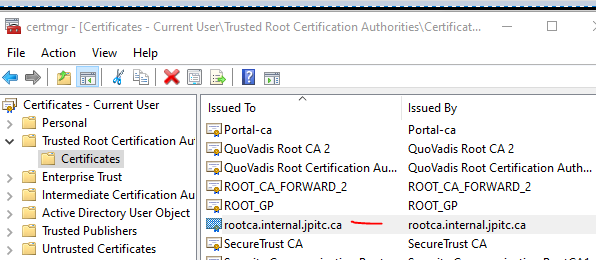
run:certmgr.msc
go on a website and validate the issuer is the sub-ca
Check the traffic log to make sure the GP traffic is decrypted