1. What is it Link to heading
Decryption profile allow the Palo Alto to do different kind of checks for decrypted/non-decrypted traffic.
They are not required to make decryption works as we saw in previous post, but are recommended.
To see the Iron Skillet recommended config go here: Iron Skillet
2. Why do this Link to heading
Palo Alto recommend the use of decryption profile in order to make encrypted/non-encrypted traffic more secure.
Uses cases examples:
- block access to expired certificates
- block access to untrusted issuers of certificates
- block access based on certification verification status (CRL/OCSP)
- block access to unsupported cipher version/suite
This give you more control on sessions allowed by the Palo Alto.
3. Diagram Link to heading
This is the same Lab as created in the other video previously.
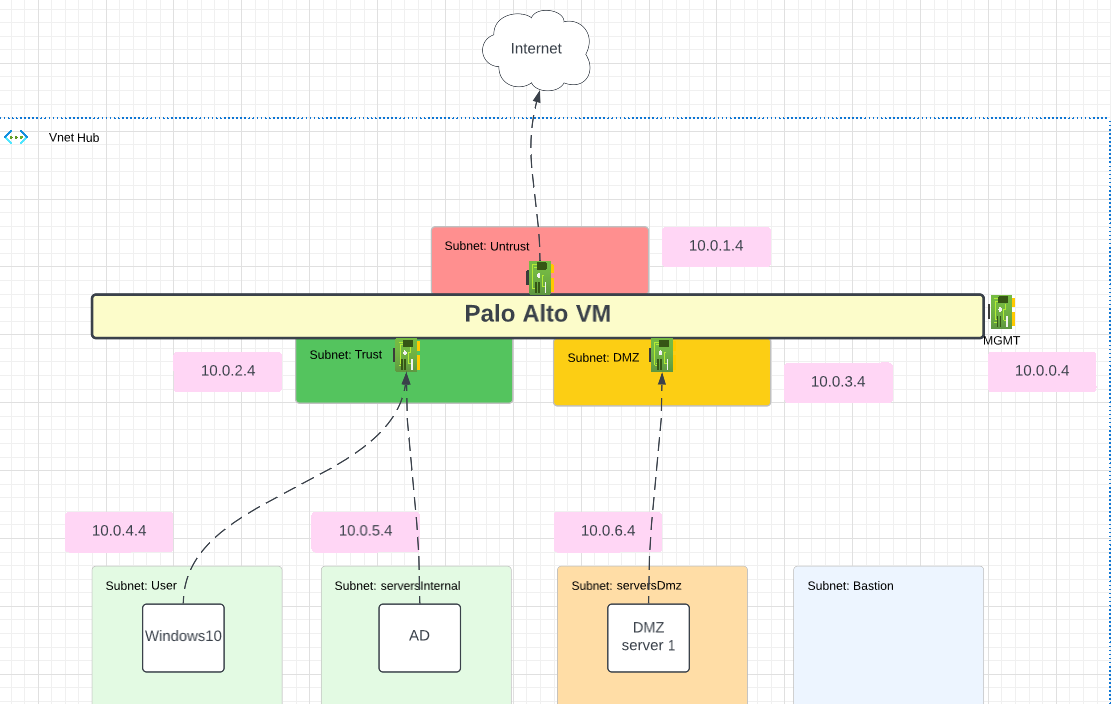
The default route for W10 and AD is the Trust NIC of the Palo Alto in Azure.
To follow me with this lab, you can go to my other post that show how to deploy that lab in Azure with Terraform: Lab Deployment Post
To configure decryption uses one of the following:
4. Lab Link to heading
4.1 Palo Alto Link to heading
4.1.1 Expired certificates Link to heading
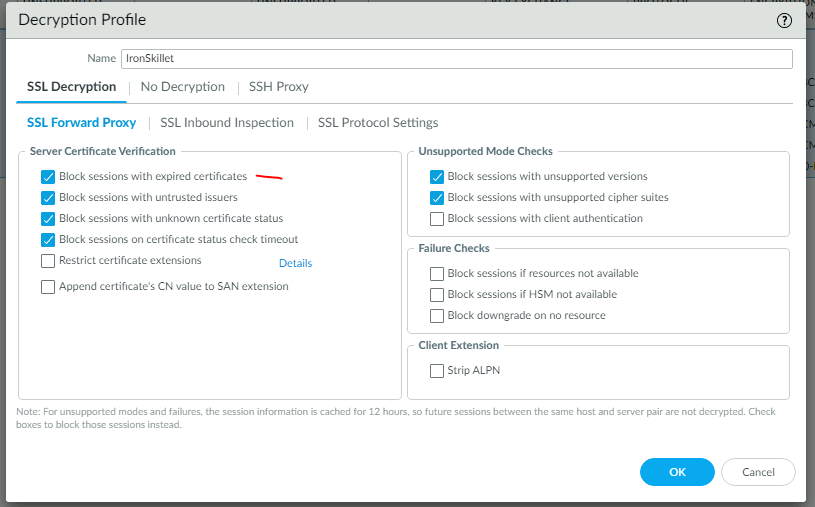
Iron Skillet recommendation: Block sessions with expired certificates
- For decrypted traffic
- For non-decrypted traffic
We wil then apply the decryption profile to the decryption policy.
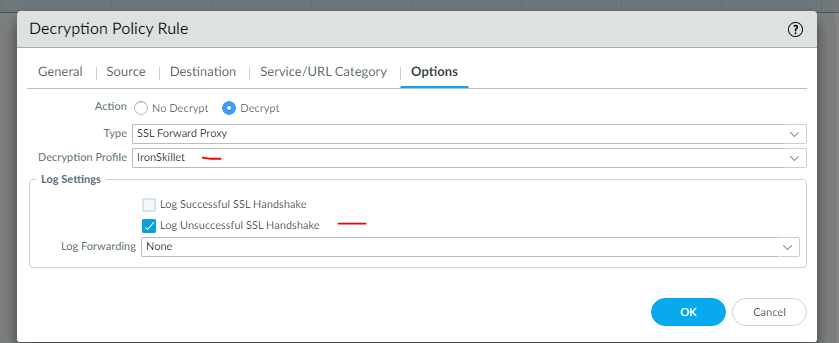
commit
Now go on the following website to test different parameter for decryption: badssl.com
without the decryption profile you would get a warning that is asking you to continue and you would still have access to the page.
with the decryption profile, the site is blocked.
In that case, palo will inserted a Response page to the user to block the website.
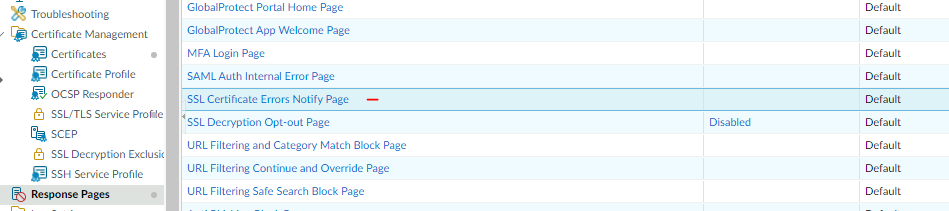
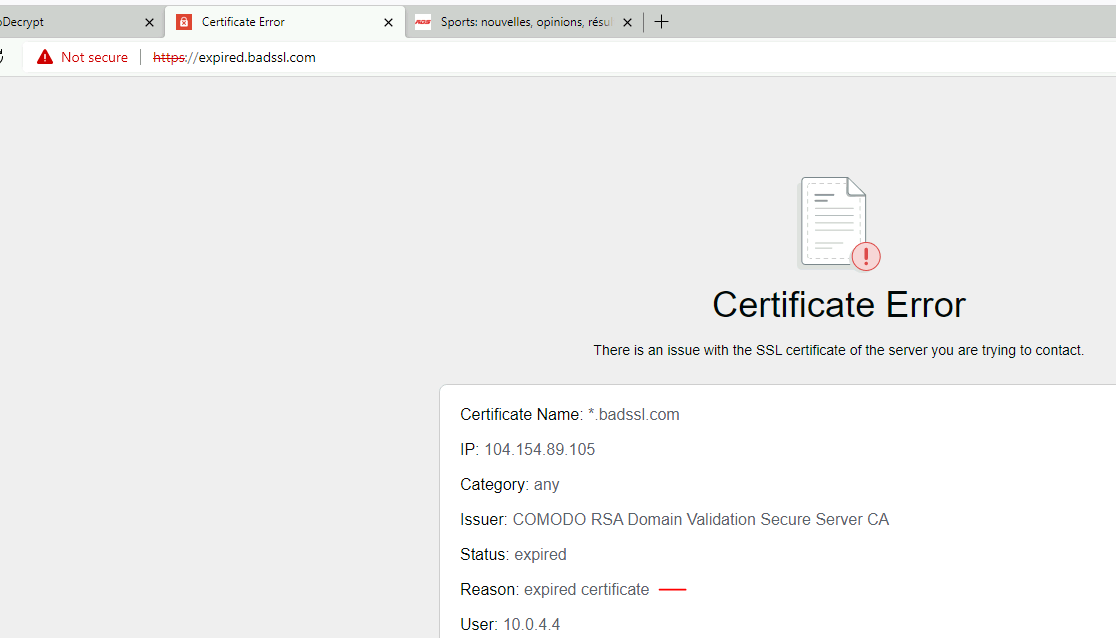
you can check the Palo Alto decryption logs and filter with the following
( error contains 'Expired server certificate' )
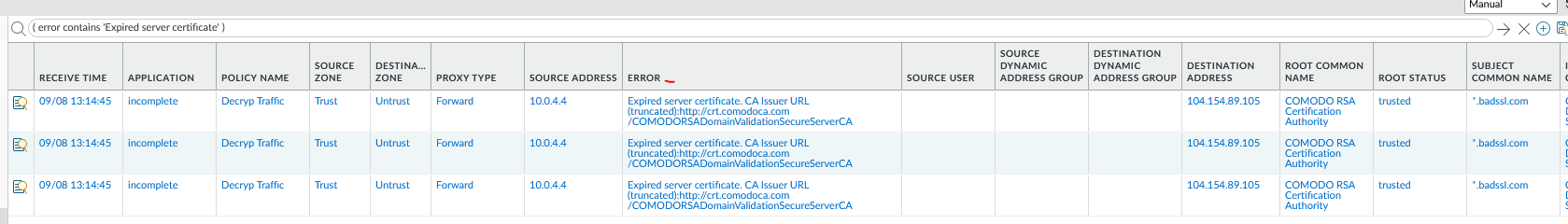
Also if you go into the traffic log you should see that the session end reason is because of decrypt error
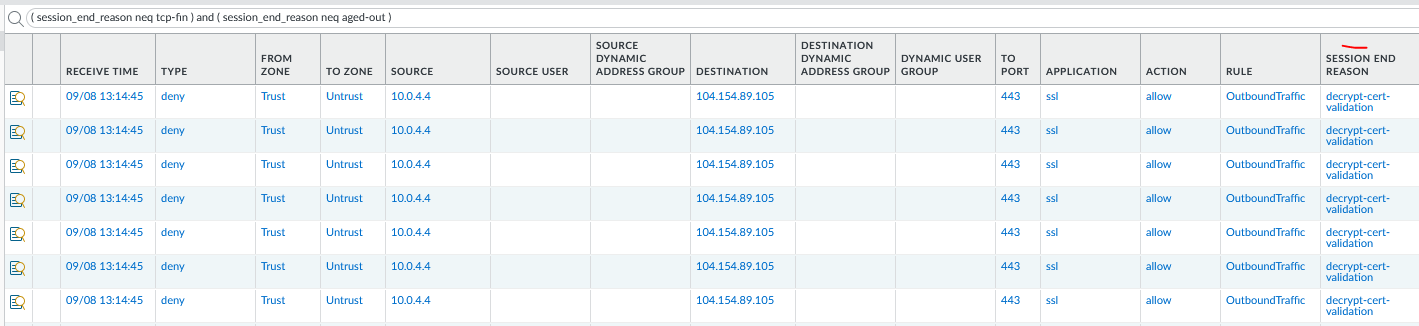
Finally, you could also check certificate already expired or that will expire soon by filtering decryption logs by: Certificate End Date.
4.1.2 Untrust issuers Link to heading
The second element in the decryption profile is to block session with Untrust issuers.
An untrust issuers is a CA that sign the web server certificate that is not trusted.
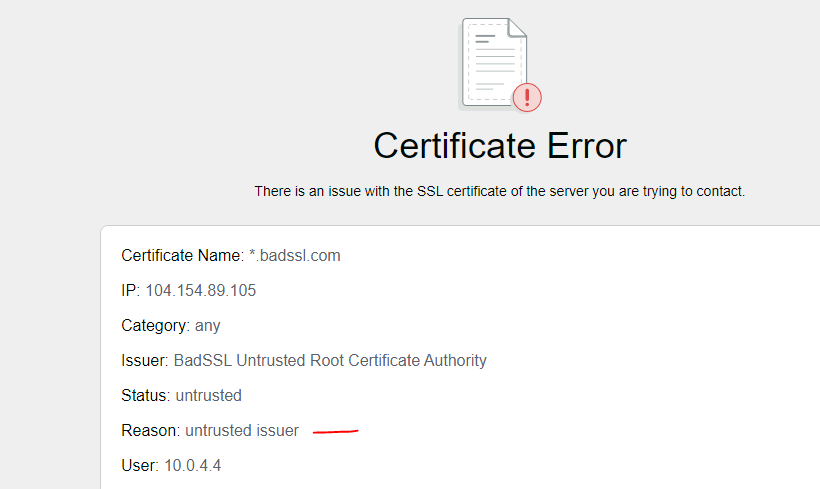
To test this go into the previous badssl website, and click on untrusted-root link
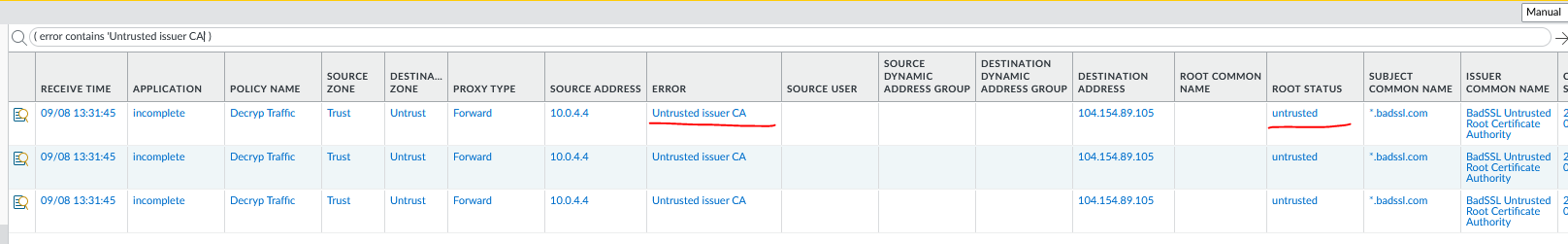
to search logs for this in the palo, use the decryption filter:
( error contains 'Untrusted issuer CA' )
4.1.3 Certificate verification Link to heading
The 2 next check are:
- Block sessions with unknown certificate status
- Block sessions on certificate status check timeout
These will block sessions based on the result or not of Certificate validation protocol
4.1.4 Unsupported mode Link to heading
Block sessions with unsupported versions: Link to heading
If we follow Palo best practices, we should allow a minimum version of TLS 1.2
If we encouter a website using ssl,tls1.0 or tls1.1, the session will be block, If there is a business need to access these websites, the best solution is to create an exception with a specific decryption policy/profile.
A way to troubleshoot this is with the bitmask in the decryption Error logs
('Clientand decrypt profile mismatch')
Basically it will tell you what bitmask the client is supporting vs what the decryption profil support.
then in cli you can check the value of the bitmask
debug dataplane show ssl-decrypt bitmask-version 0x08 (TLS1.0)
In a similar way you can decide to allow/block cipher suites You can also decide to block sessions that does client authentication.
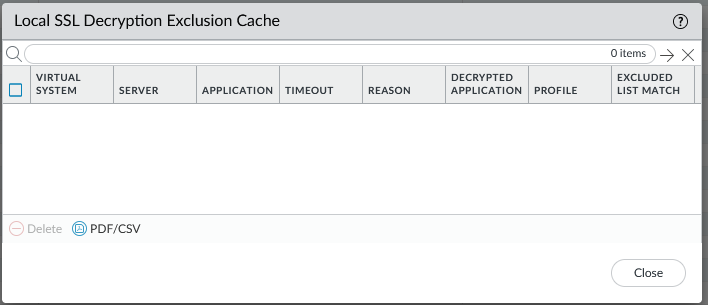
If sessions block are not check for this parameters, palo will add the server to the Local Decryption Exclusion Cache for 12 hours.
Client Authentication is a common reason to exclude traffic from decryption, this is why palo alto recommends to allow it as a best practice.
If in the next 12 hours there is traffic to the same server, Palo will bypass decryption
4.1.5 Other checks Link to heading
failure check Link to heading
This is mainly to block/allow sessions in case there is not enough resources on the firewall to decrypt the traffic.
Strip ALPN Link to heading
I will do another video about HTTP/2 and QUIC
No decrypt traffic Link to heading
Take note that you can still bock sessions from expired certificate and untrusted issuers for non-decrypted traffic, and this is considered a best practice.